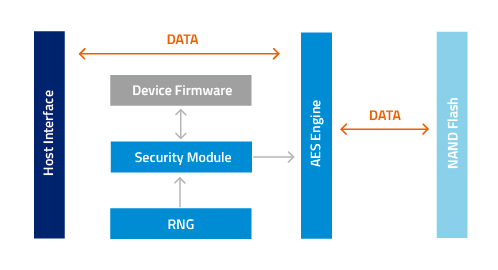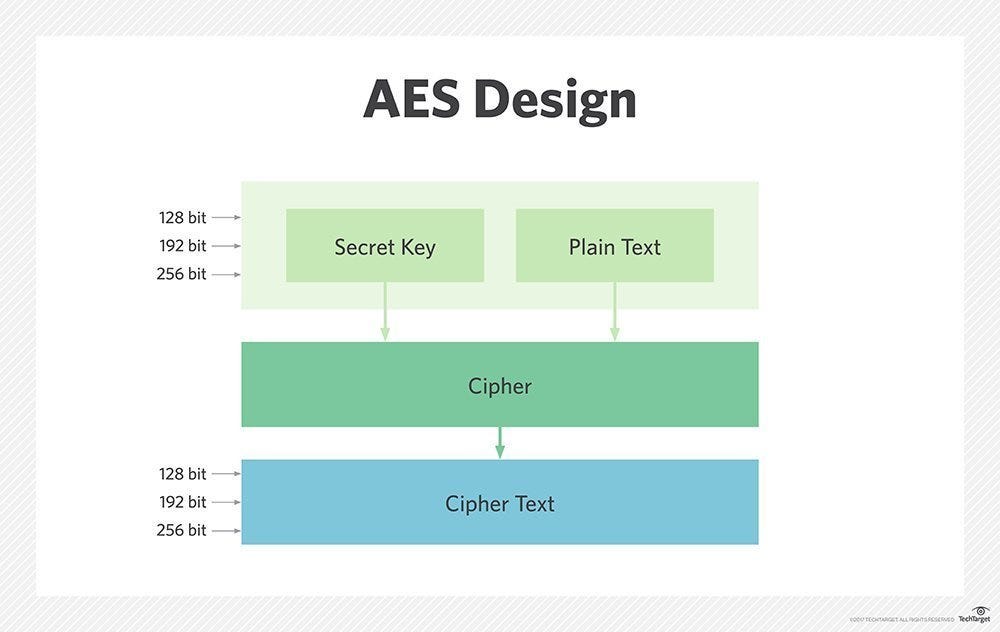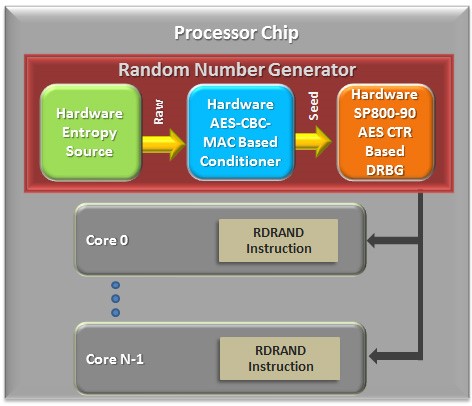
Intel® Hardware-based Security Technologies Bring Differentiation to Biometrics Recognition Applications Part 2 - CodeProject

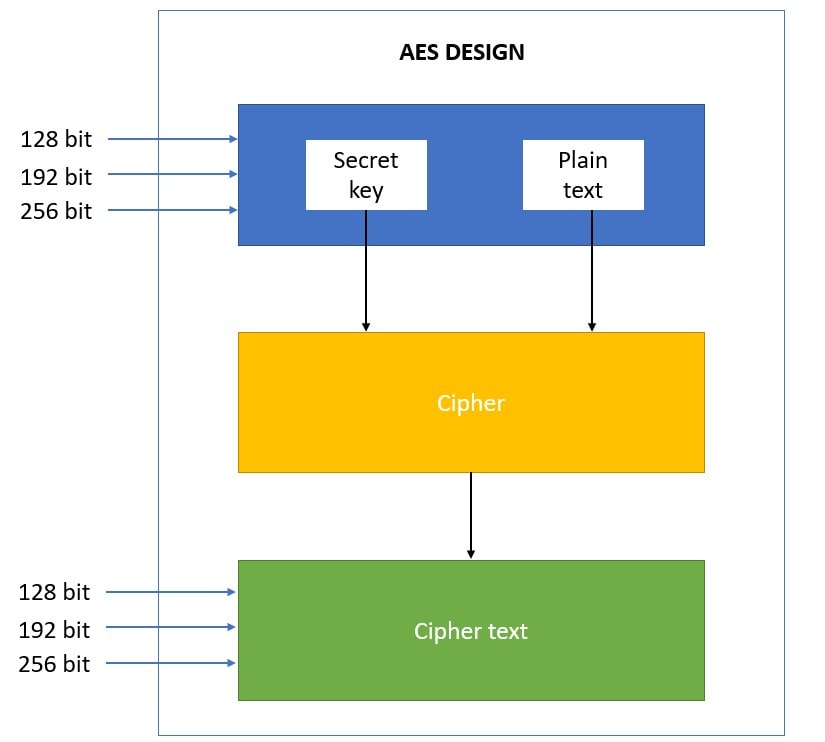
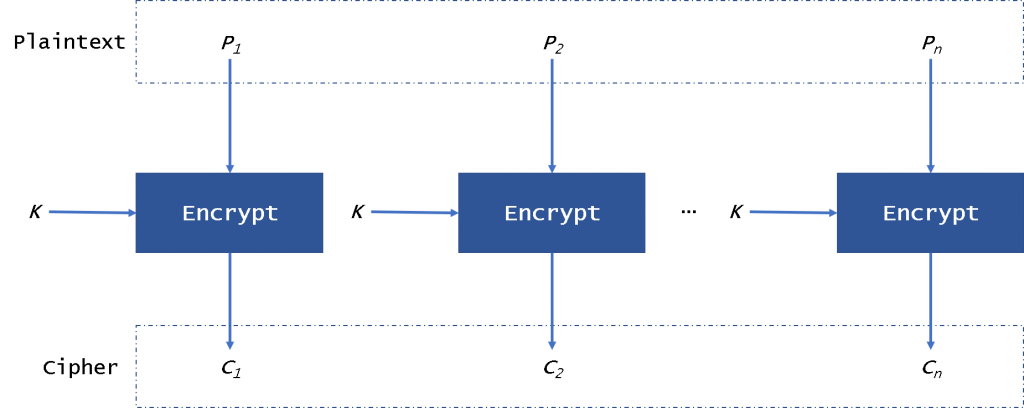
encryption - When using AES and CBC, is it necessary to keep the IV secret? - Information Security Stack Exchange
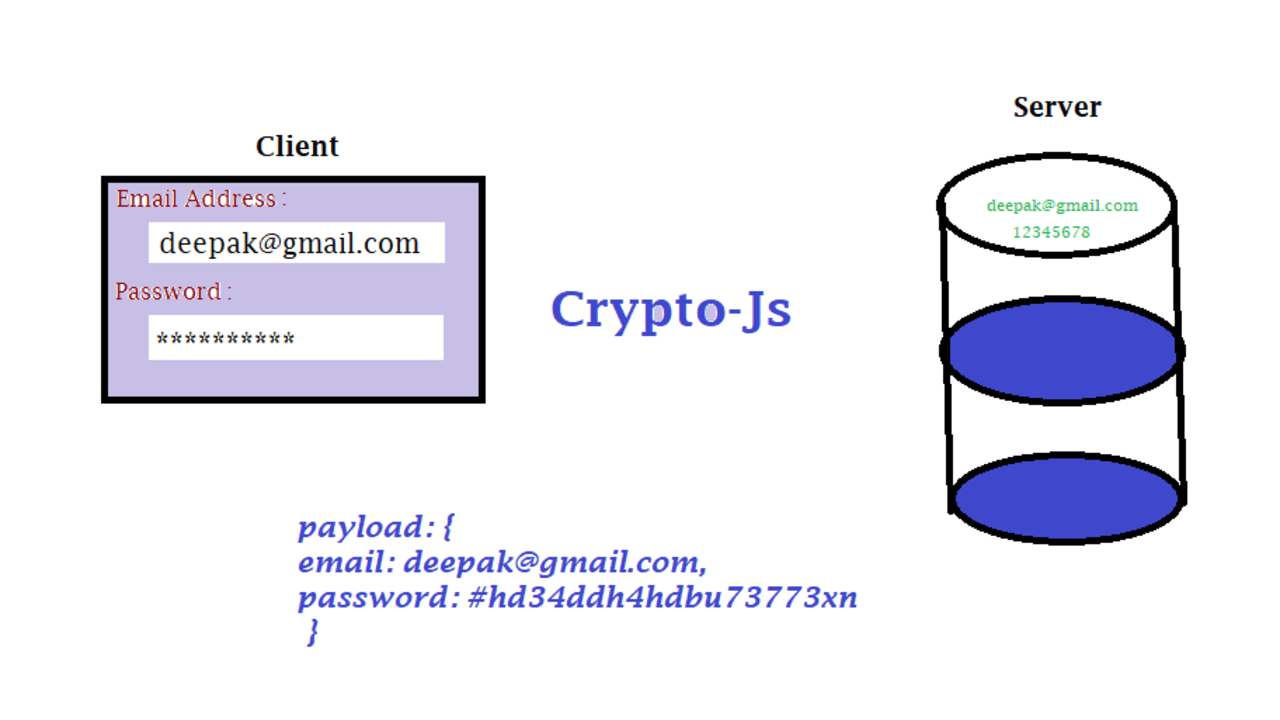
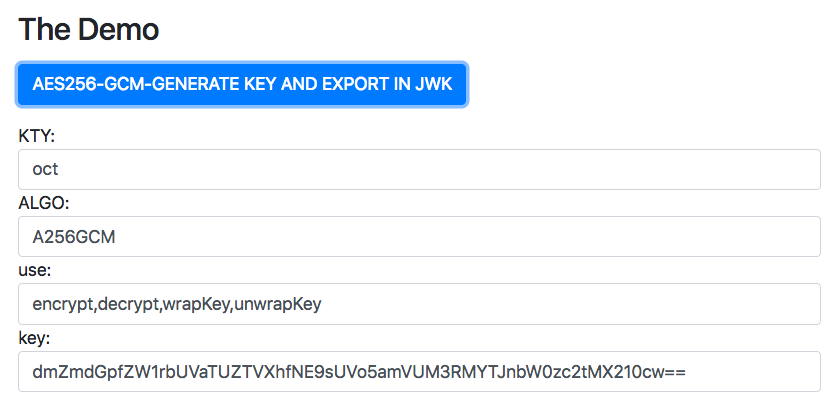
End-to-End Data Security:Shielding API Payloads through CryptoJS and Java AES-256 Encryption” | by Shivam Jaswal | Medium
Crypto.createDecipheriv() using aes-256-cbc on an encrypted XML document · Issue #2896 · nodejs/help · GitHub